Table of Contents
Entra ID Connect Error 8344
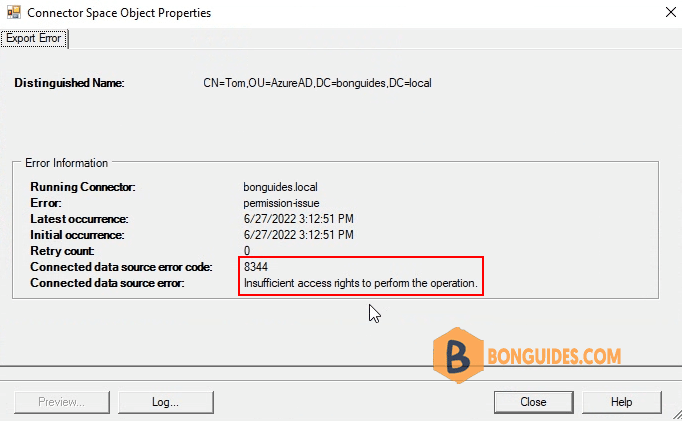
With Entra ID Replication, you may notice that you have the following error when you take a look at your connector status:
- Error: permission-issue
- Connected data source error code: 8344
- Connected data source error: Insufficient access rights to perform this operation.
Solution 1: Grant permission for the service account
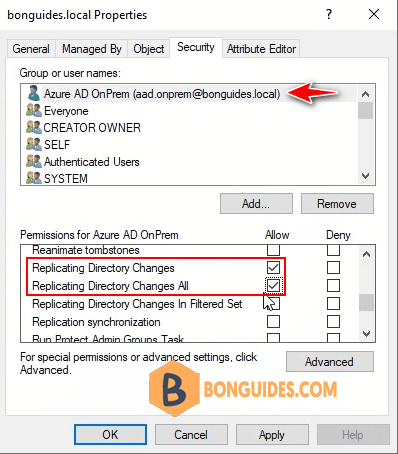
1. Firstly ensure that the user you are running AAD sync under, has the following permissions on the root of your local AD domain. Minimum permission required for the service account are:
- Replicate directory changes
- Replicate directory changes all
- Write permission , for attribute ms-ds-consistencyguid
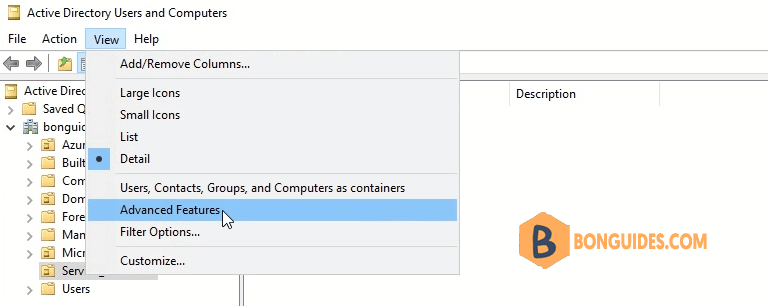
2. Open ADUC then enable Advanced Features view.
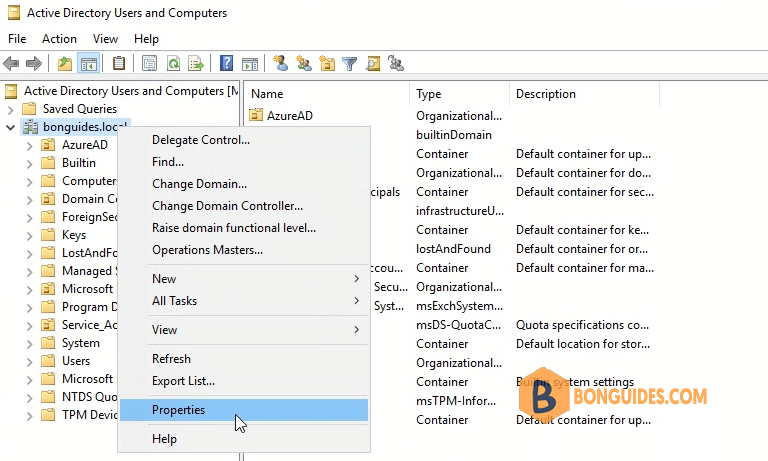
3. Right click on the root of your local domain then select Properties.
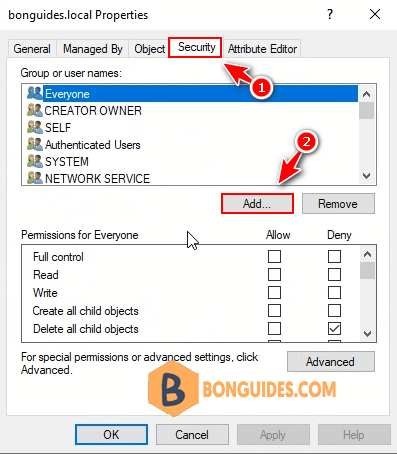
5. Add required permissions for the service account Replicate directory changes and Replicate directory changes all.
6. Add write permission for attribute ms-ds-consistencyguid for the service account.
$accountName = "DOMAINNAME\USERNAME"
$ForestDN = "DC=DOMAINNAME,DC=com"
$cmd = "dsacls '$ForestDN' /I:S /G '`"$accountName`":WP;ms-ds-consistencyGuid;user'"
Invoke-Expression $cmdResult in my test environment:
PS C:\Users\Administrator> $accountName = "bonguides\aad.onprem"
PS C:\Users\Administrator> $ForestDN = "DC=bonguides,DC=local"
PS C:\Users\Administrator> $cmd = "dsacls '$ForestDN' /I:S /G '`"$accountName`":WP;ms-ds-consistencyGuid;user'"
PS C:\Users\Administrator> Invoke-Expression $cmd
Owner: BUILTIN\Administrators
Group: BUILTIN\Administrators
Access list:
Deny Everyone SPECIAL ACCESS
DELETE CHILD
Allow BONGUIDES\aad.onprem SPECIAL ACCESS
READ PERMISSONS
LIST CONTENTS
READ PROPERTY
Permissions inherited to subobjects are:
Inherited to all subobjects
Allow BUILTIN\Administrators SPECIAL ACCESS
DELETE
READ PERMISSONS
WRITE PERMISSIONS
--------------------------------------------------------
READ PROPERTY
Allow NT AUTHORITY\SELF SPECIAL ACCESS for msTPM-TpmInformationForComputer
WRITE PROPERTY
The command completed successfully
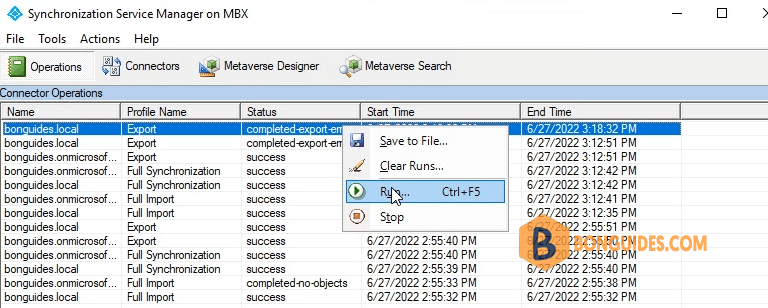
PS C:\Users\Administrator>7. Now, run the connector to verify it works and see data updated into Metaverse.
Solution 2: Enable inheritance for users
After that the sync would start to run and I notice that are still some accounts giving “permission issue” error. So the next dependency was looking into the “inheritance” function, was it disable or not.
I was able to identify that the particular OU have its inheritance enabled but on the single user object inside that OU, its inheritance was disabled.
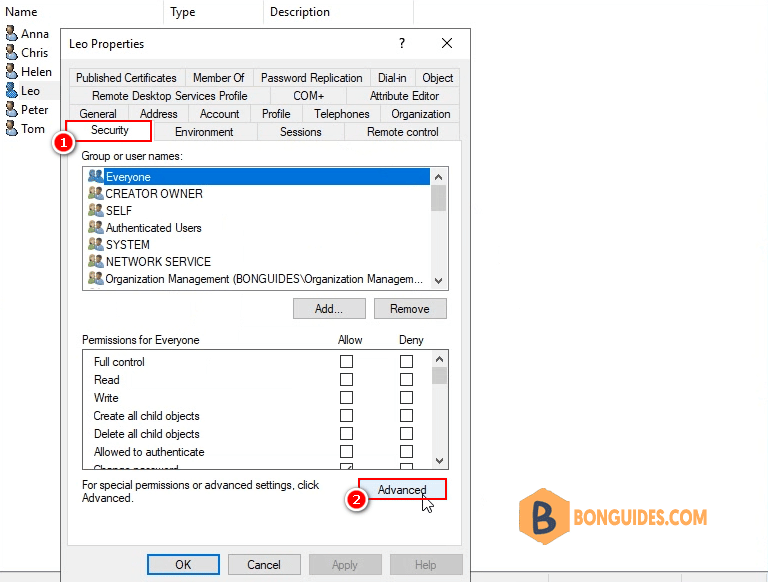
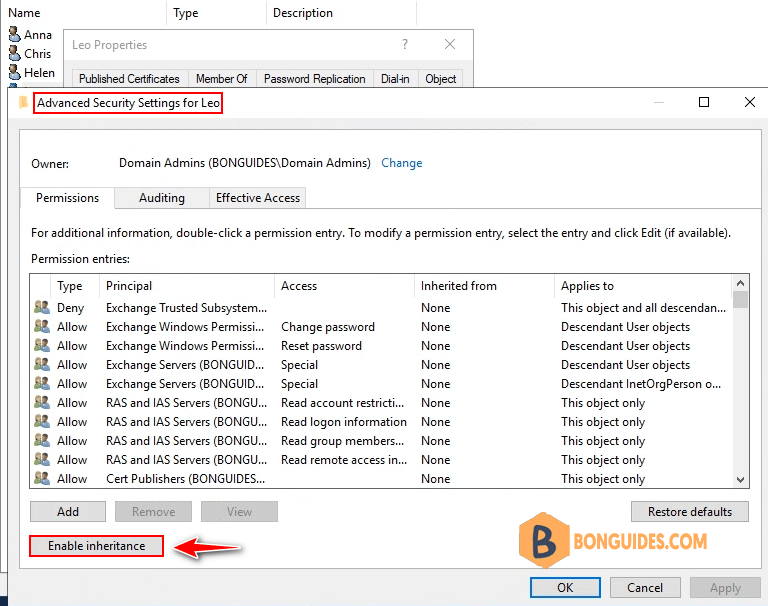
Let enable inheritance for the user then run connector again.
Solution 3:
In some cases, even the user is enabled inheritance and the permissions of the service account are configured correctly. Some users still cannot sync with permission issue.
Most times, this isn’t sufficient, you will have to add the service account as a member of the Administrator’s group in Active Directory.
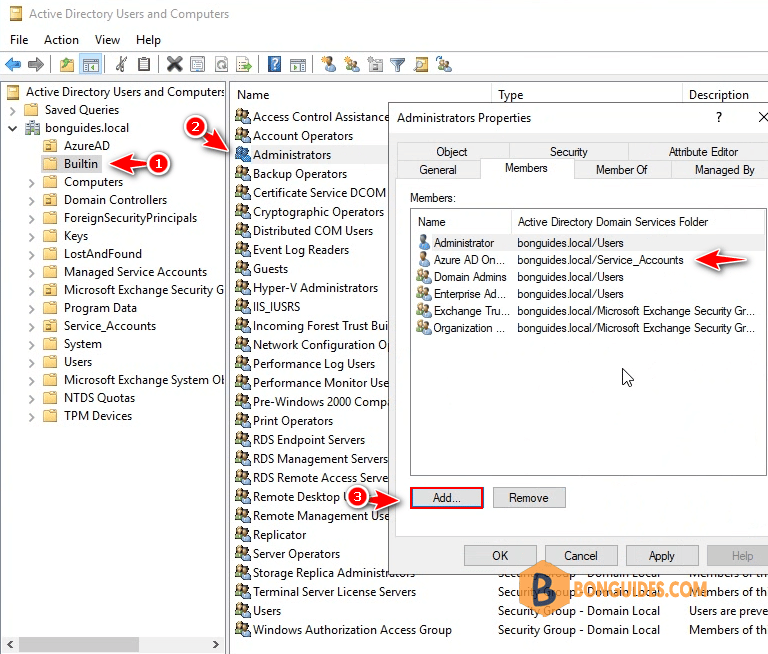
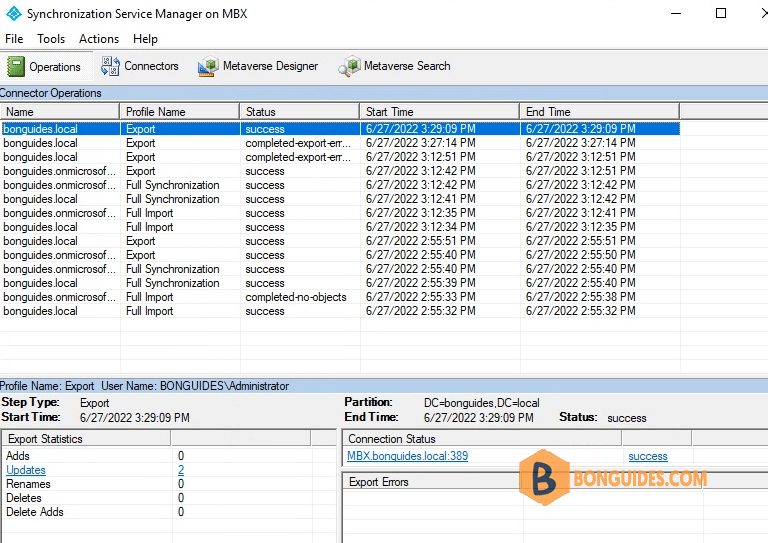
Re-run the connector, and all users should be update to Metaverse then sync to Entra ID without any problems.
Not a reader? Watch this related video tutorial:





Thanks! THis helped tremendously!