Table of Contents
Applications registered in an Azure Active Directory (Entra ID) tenant are, by default, available to all users of the tenant who authenticate successfully.
Similarly, in a multi-tenant application, all users in the Entra ID tenant where the application is provisioned can access the application once they successfully authenticate in their respective tenant.
Tenant administrators and developers often have requirements where an application must be restricted to a certain set of users or apps (services). There are two ways to restrict an application to a certain set of users, apps or security groups:
- Developers can use popular authorization patterns like Azure role-based access control (Azure RBAC).
- Tenant administrators and developers can use built-in feature of Entra ID.
Supported app configurations
The option to restrict an app to a specific set of users, apps or security groups in a tenant works with the following types of applications:
- Applications configured for federated single sign-on with SAML-based authentication.
- Application proxy applications that use Entra ID preauthentication.
- Applications built directly on the Entra ID application platform that use OAuth 2.0/OpenID Connect authentication after a user or admin has consented to that application.
Configure the app to require user assignment
1️⃣ Sign in to the Microsoft Entra admin center.
2️⃣ Under Identity, select Enterprise Applications then select All applications.
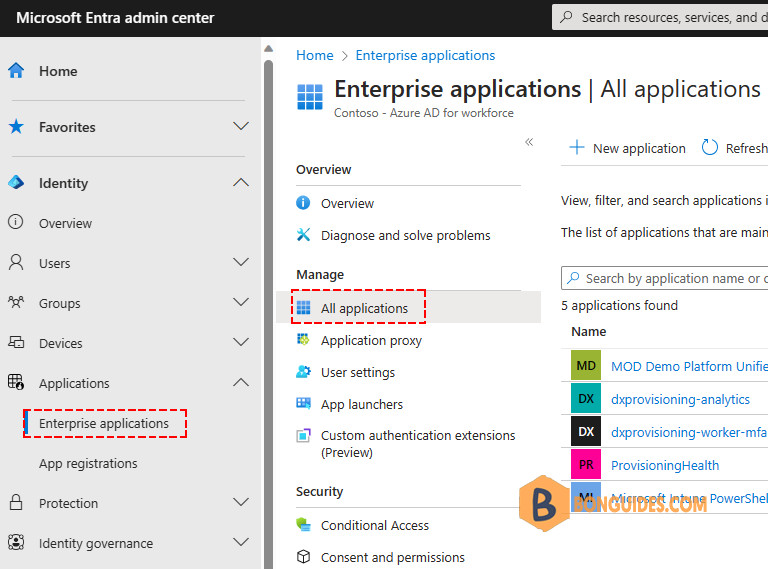
3️⃣ Select the application you want to configure to require assignment. Use the filters at the top of the window to search for a specific application. For example, we selected Microsoft Intune PowerShell app.
4️⃣ On the application’s Overview page, under Manage, select Properties.
5️⃣ Locate the setting Assignment required? and set it to Yes. When this option is set to Yes, users and services attempting to access the application or services must first be assigned for this application, or they won’t be able to sign-in or obtain an access token.
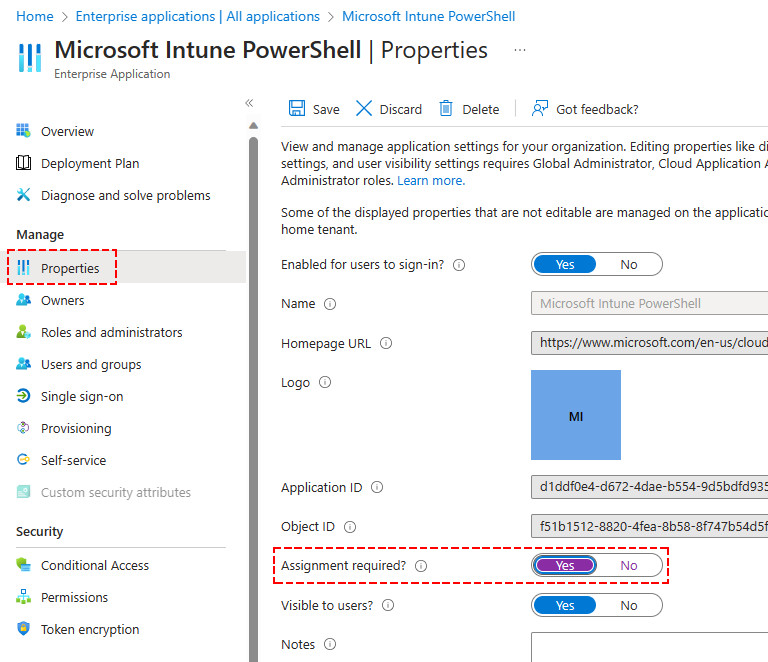
6️⃣ Select Save on the top bar.
When an application requires assignment, user consent for that application isn’t allowed. This is true even if users consent for that app would have otherwise been allowed. Be sure to grant tenant-wide admin consent to apps that require assignment.
Assign the app to users and groups to restrict access
Once you’ve configured your app to enable user assignment, you can go ahead and assign the app to users and groups.
1️⃣ Under Manage, select the Users and groups then select Add user/group.
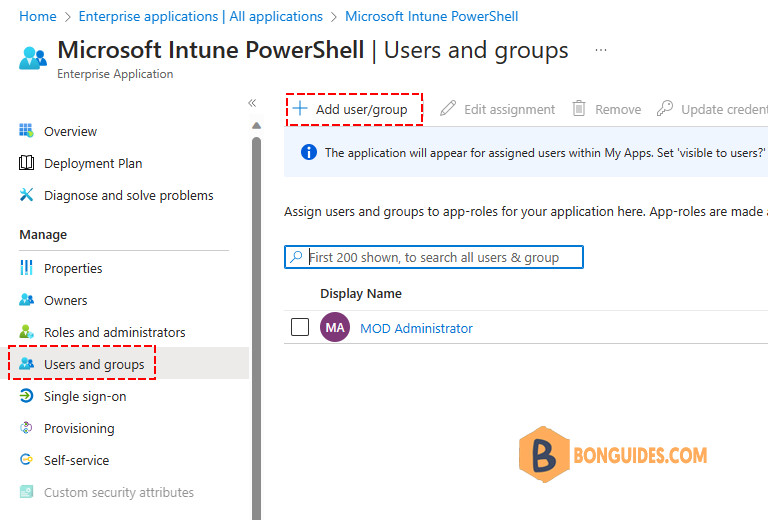
2️⃣ Select the Users selector. A list of users and security groups are shown along with a textbox to search and locate a certain user or group. This screen allows you to select multiple users and groups in one go.
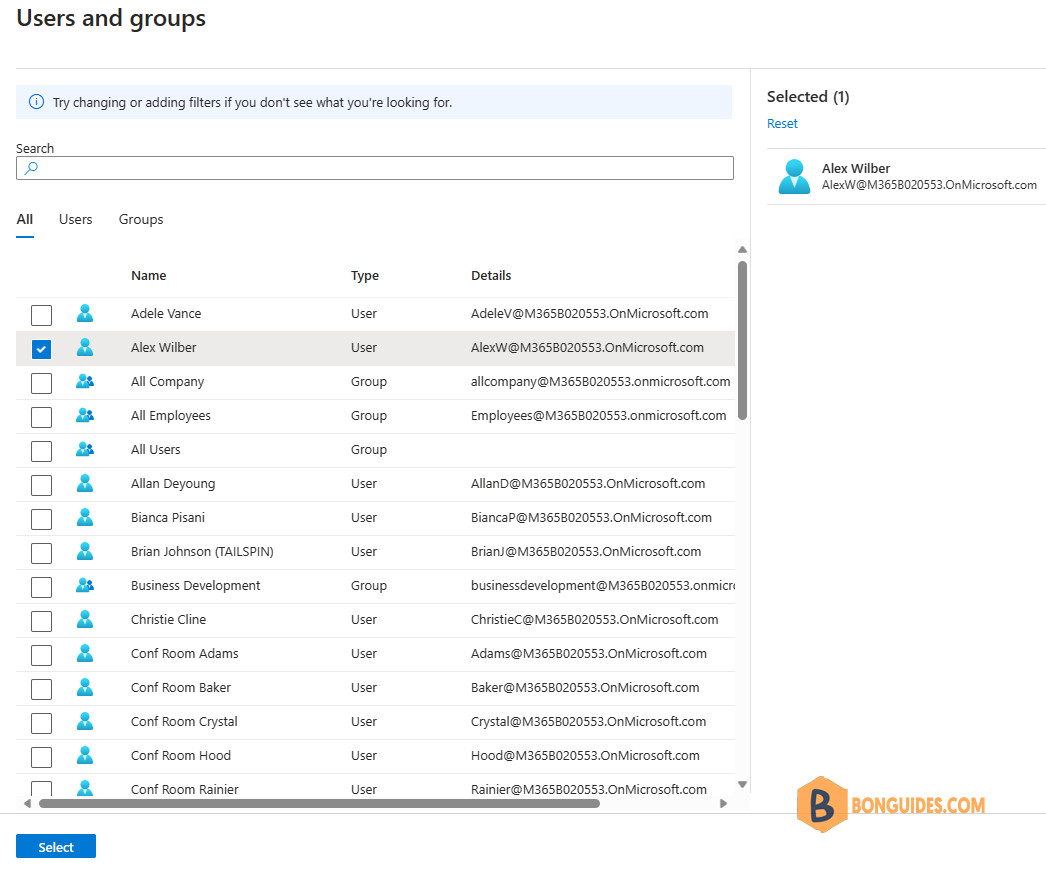
3️⃣ Once you’re done selecting the users and groups. Select Assign to complete the assignments of the app to the users and groups. Confirm that the users and groups you added are showing up in the updated Users and groups list.
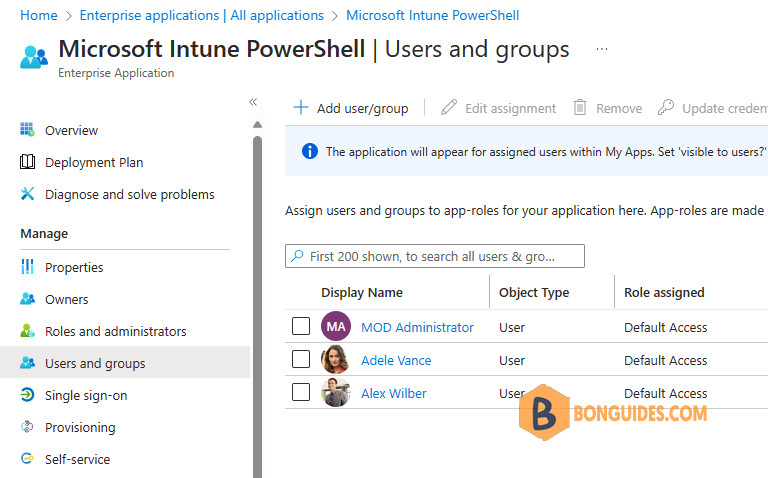
As you can see, only assigned users can be access the app that we have configured.
PS C:\> Connect-MSGraph
UPN TenantId
--- --------
[email protected] 09e3c00a-3596-42f5-abcf-6614a2865157
Read more: Microsoft document.
Not a reader? Watch this related video tutorial:




