Table of Contents
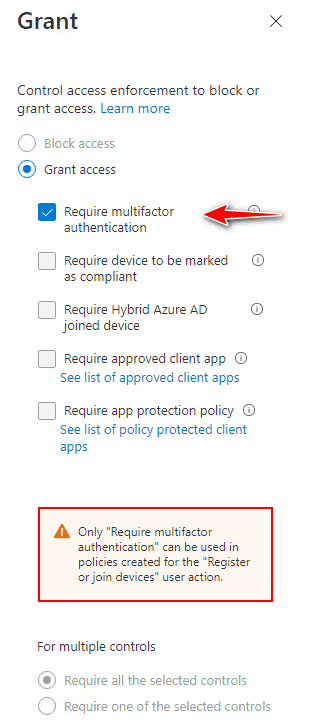
Require MFA for Entra ID join
Azure Active Directory that brings more granularity to the MFA requirement for device registration and Entra ID domain join.
Because this setting was having some caveats and causing some inconvenience for end-users, this setting was mostly disabled, despite the fact that this is not the recommended option.

Disable Require MFA for Entra ID Domain Join
Note: It is recommended to enforce MFA before a user can register or join their device to Entra ID. This ensures that compromised accounts cannot be used to add rogue devices to Azure Active Directory.
To disable Require MFA for Entra ID Domain Join:
1. Login into Azure Active Directory using a global admin account.
2. Select Azure Active Directory then select Devices under Manage section.
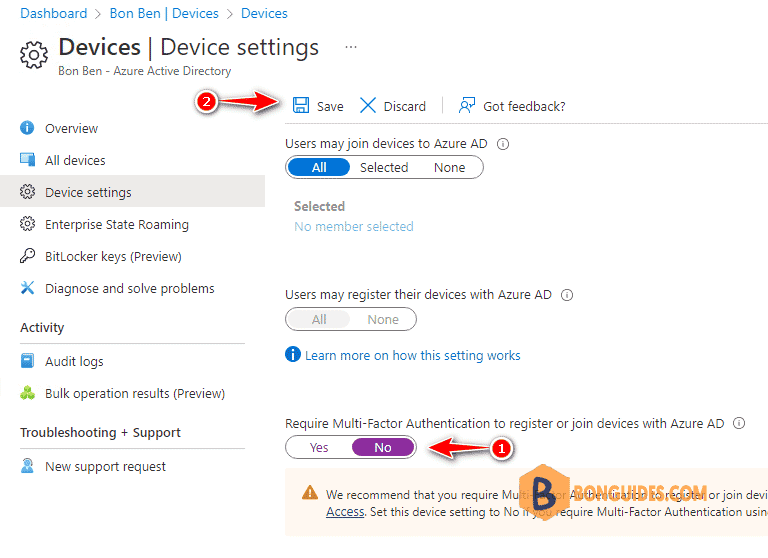
Finally, try to joining a device to Entra ID to verify it works.
More granularity
Microsoft released a new user action in Entra ID Conditional Access that ultimately replaces this previous setting.

With Conditional Access you can configure require MFA when register or join action for specific users, groups, or roles. You are also able to use some conditions like device platform and locations. Sign-in and user risk are also available. To give you some examples of what you can do:
- Require MFA for device registration from untrusted locations only.
- Require MFA for device registration when user risk is medium or higher.
- Require MFA for specific operating systems like Android or iOS.
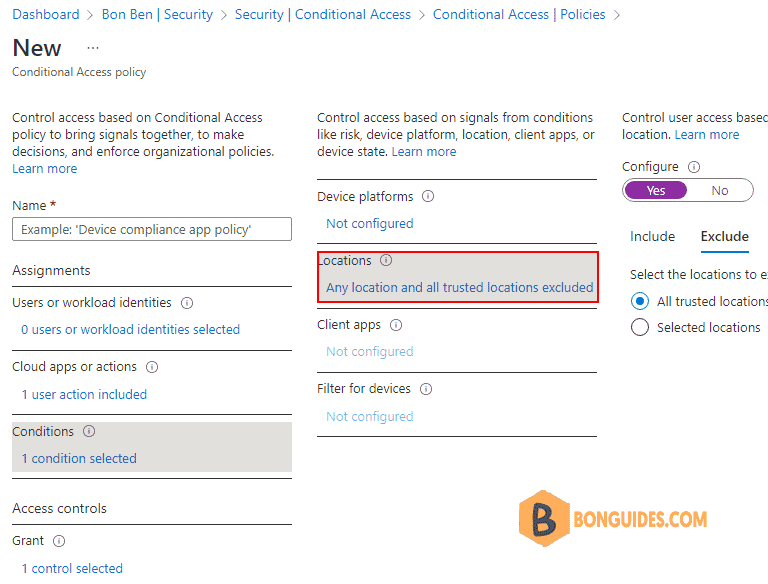
Currently, this user action only allows you to enable MFA as a control when users register or join devices to Entra ID. Other controls that are dependent on or not applicable to Entra ID device registration are disabled with this user action.