Table of Contents
PowerShell’s execution policy is a safety feature that controls the conditions under which PowerShell loads configuration files and runs scripts. This feature helps prevent the execution of malicious scripts.
On a Windows computer you can set an execution policy for:
- The local computer
- The current user
- Or for a particular session.
You can also use a Group Policy setting to set execution policies for computers and users.
Execution policies for the local computer and current user are stored in the registry. You don’t need to set execution policies in your PowerShell profile. The execution policy for a particular session is stored only in memory and is lost when the session is closed.
On non-Windows computers, the default execution policy is Unrestricted and cannot be changed. The Set-ExecutionPolicy cmdlet is available, but PowerShell displays a console message that it’s not supported. While Get-ExecutionPolicy returns Unrestricted on non-Windows platforms, the behavior really matches Bypass because those platforms do not implement the Windows Security Zones.
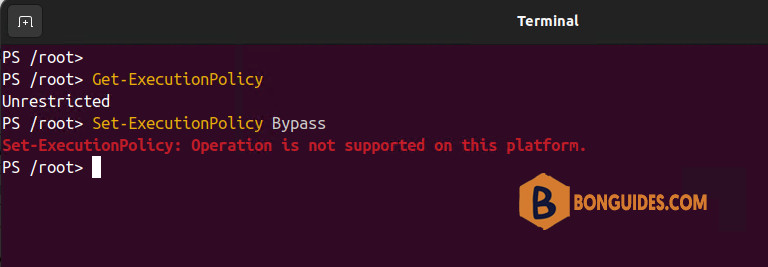
PowerShell execution policies
Enforcement of these policies only occurs on Windows platforms. The PowerShell execution policies are as follows:
AllSigned
- Scripts can run.
- Requires that all scripts and configuration files be signed by a trusted publisher, including scripts that you write on the local computer.
- Prompts you before running scripts from publishers that you haven’t yet classified as trusted or untrusted.
- Risks running signed, but malicious, scripts.
Bypass
- Nothing is blocked and there are no warnings or prompts.
- This execution policy is designed for configurations in which a PowerShell script is built in to a larger application or for configurations in which PowerShell is the foundation for a program that has its own security model.
Default
- Sets the default execution policy.
- Restricted for Windows clients.
- RemoteSigned for Windows servers.
RemoteSigned
- The default execution policy for Windows server computers.
- Scripts can run.
- Requires a digital signature from a trusted publisher on scripts and configuration files that are downloaded from the internet which includes email and instant messaging programs.
- Doesn’t require digital signatures on scripts that are written on the local computer and not downloaded from the internet.
- Runs scripts that are downloaded from the internet and not signed, if the scripts are unblocked, such as by using the
Unblock-Filecmdlet. - Risks running unsigned scripts from sources other than the internet and signed scripts that could be malicious.
Restricted
- The default execution policy for Windows client computers.
- Permits individual commands, but does not allow scripts.
- Prevents running of all script files, including formatting and configuration files (
.ps1xml), module script files (.psm1), and PowerShell profiles (.ps1).
Undefined
- There is no execution policy set in the current scope.
- If the execution policy in all scopes is Undefined, the effective execution policy is Restricted for Windows clients and RemoteSigned for Windows Server.
Unrestricted
- The default execution policy for non-Windows computers and cannot be changed.
- Unsigned scripts can run. There is a risk of running malicious scripts.
- Warns the user before running scripts and configuration files that are not from the local intranet zone.
Execution policy scope
You can set an execution policy that is effective only in a particular scope.
The valid values for Scope are MachinePolicy, UserPolicy, Process, CurrentUser, and LocalMachine.
LocalMachine is the default when setting an execution policy.
The Scope values are listed in precedence order. The policy that takes precedence is effective in the current session, even if a more restrictive policy was set at a lower level of precedence.
- MachinePolicy: Set by a Group Policy for all users of the computer.
- UserPolicy: Set by a Group Policy for the current user of the computer.
- Process: The Process scope only affects the current PowerShell session. The execution policy is saved in the environment variable $env:PSExecutionPolicyPreference, rather than the registry. When the PowerShell session is closed, the variable and value are deleted.
- CurrentUser: The execution policy affects only the current user. It’s stored in the HKEY_CURRENT_USER registry subkey.
- LocalMachine: The execution policy affects all users on the current computer. It’s stored in the HKEY_LOCAL_MACHINE registry subkey.
Managing the execution policy with PowerShell
To get the effective execution policy for the current PowerShell session, use the Get-ExecutionPolicy cmdlet. The following command gets the effective execution policy:
Get-ExecutionPolicy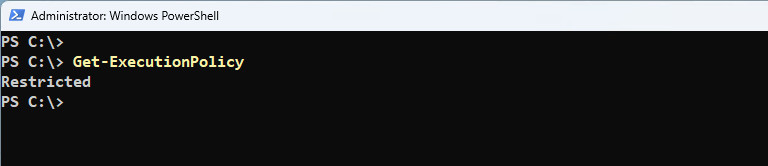
To get all of the execution policies that affect the current session and display them in precedence order:
Get-ExecutionPolicyPS C:\> Get-ExecutionPolicy -List
Scope ExecutionPolicy
----- ---------------
MachinePolicy Undefined
UserPolicy Undefined
Process Undefined
CurrentUser RemoteSigned
LocalMachine AllSignedIn this case, the effective execution policy is RemoteSigned because the execution policy for the current user takes precedence over the execution policy set for the local computer.
To get the execution policy set for a particular scope, use the Scope parameter of Get-ExecutionPolicy. For example, the following command gets the execution policy for the CurrentUser scope:
PS C:\> Get-ExecutionPolicy -Scope CurrentUser
RemoteSigned
PS C:\> Get-ExecutionPolicy -Scope LocalMachine
AllSignedChange the execution policy
To change the PowerShell execution policy on your Windows computer, use the Set-ExecutionPolicy cmdlet.
- If you set the execution policy for the scopes LocalMachine or the CurrentUser, the change is saved in the registry and remains effective until you change it again.
If you set the execution policy for the Process scope, it’s not saved in the registry. The execution policy is retained until the current process and any child processes are closed.
For example, change your execution policy:
#<PolicyName> [AllSign, Bypass, Default, RemoteSinged, Restricted, Undefined, Unrestricted]
Set-ExecutionPolicy -ExecutionPolicy <PolicyName>
Set-ExecutionPolicy -ExecutionPolicy RemoteSignedWhen changing the execution policy, PowerShell shows a warning message and asked you to confirm the action. To avoid this, you can use the -Force parameter.
Set-ExecutionPolicy -ExecutionPolicy AllSigned -Scope LocalMachine -ForceExecution Policy Change
The execution policy helps protect you from scripts that you do not trust. Changing
the execution policy might expose you to the security risks described in the
about_Execution_Policies help topic at
https:/go.microsoft.com/fwlink/?LinkID=135170. Do you want to change the execution
policy?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help
(default is "N"):To set the execution policy in a particular scope:
#<PolicyName> [AllSign, Bypass, Default, RemoteSinged, Restricted, Undefined, Unrestricted]
#scope> [MachinePolicy, UserPolicy, Process, CurrentUser, LocalMachine]
Set-ExecutionPolicy -ExecutionPolicy <PolicyName> -Scope <scope>
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUserSometimes, a command to change an execution policy can succeed but still not change the effective execution policy. For example, a command that sets the execution policy for the local computer can succeed but be overridden by the execution policy for the current user.
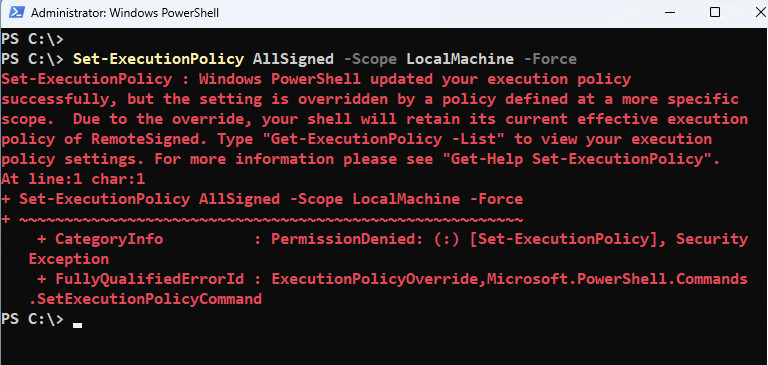
Remove the execution policy
To remove the execution policy for a particular scope, set the execution policy to Undefined. For example, to remove the execution policy for all the users of the local computer:
PS C:\> Get-ExecutionPolicy -List
Scope ExecutionPolicy
----- ---------------
MachinePolicy Undefined
UserPolicy Undefined
Process Undefined
CurrentUser RemoteSigned
LocalMachine AllSigned
PS C:\> Set-ExecutionPolicy Undefined -Scope LocalMachine -Force
PS C:\> Get-ExecutionPolicy -List
Scope ExecutionPolicy
----- ---------------
MachinePolicy Undefined
UserPolicy Undefined
Process Undefined
CurrentUser RemoteSigned
LocalMachine Undefined
#To remove the execution policy for a Scope:
Set-ExecutionPolicy -ExecutionPolicy Undefined -Scope CurrentUserSet a different policy for one session
When configure the execution policy for a session, the execution policy that you set isn’t stored in the registry. Instead, it’s stored in the $env:PSExecutionPolicyPreference environment variable. The variable is deleted when you close the session in which the policy is set. You cannot change the policy by editing the variable value.
PS C:\> Get-ExecutionPolicy
RemoteSigned
PS C:\> Set-ExecutionPolicy -ExecutionPolicy Bypass Process -Force
PS C:\> Get-ExecutionPolicy
Bypass
PS C:\> Set-ExecutionPolicy -ExecutionPolicy Unrestricted Process -Force
PS C:\> Get-ExecutionPolicy
UnrestrictedDuring the session, the execution policy that is set for the session takes precedence over an execution policy that is set in the registry for the local computer or current user. However, it doesn’t take precedence over the execution policy set by using a Group Policy.
Use Group Policy to Manage Execution Policy
You can use the Turn on Script Execution Group Policy setting to manage the execution policy of computers in your enterprise with Active Directory. The Group Policy setting overrides the execution policies set in PowerShell in all scopes.
The Turn on Script Execution policy settings are as follows:
- If Turn on Script Execution is not configured, it has no effect. The execution policy set in PowerShell is effective.
- If you disable Turn on Script Execution, scripts do not run. This is equivalent to the Restricted execution policy.
- If you enable Turn on Script Execution, you can select an execution policy. The Group Policy settings are equivalent to the following execution policy settings:
The PowerShellExecutionPolicy.adm and PowerShellExecutionPolicy.admx files add the Turn on Script Execution policy to the Computer Configuration and User Configuration nodes in Group Policy Editor in the following paths.
Administrative Templates\Classic Administrative Templates\Windows Components\Windows PowerShellWhen determining the effective execution policy for a session, PowerShell evaluates the execution policies in the following precedence order:
Group Policy: MachinePolicy
Group Policy: UserPolicy
Execution Policy: Process (or pwsh.exe -ExecutionPolicy)
Execution Policy: CurrentUser
Execution Policy: LocalMachineManage signed and unsigned scripts
By default, Windows marks the downloaded scripts file as coming from the Internet. If your PowerShell execution policy is RemoteSigned, PowerShell won’t run unsigned scripts that are downloaded from the internet which includes email and instant messaging programs.
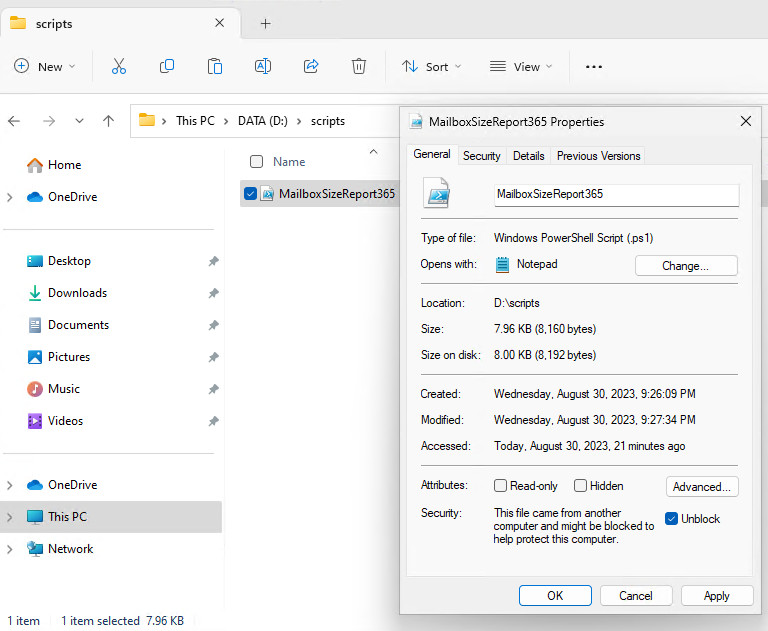
When running this type of script, you would get the following error:
The file is not digitally signed. You cannot run this script on the current system. For more information about running scripts and setting execution policy, see about_Execution_Policies at https:/go.microsoft.com/fwlink/?LinkID=135170.
You can sign the script or elect to run an unsigned script without changing the execution policy. Use the Unblock-File cmdlet to unblock the scripts so that you can run them in PowerShell.
Unblock-File -Path D:\scripts\MailboxSizeReport365.ps1Not a reader? Watch this related video tutorial:




